Frühere Suchanfragen
Suchoptionen
#rat
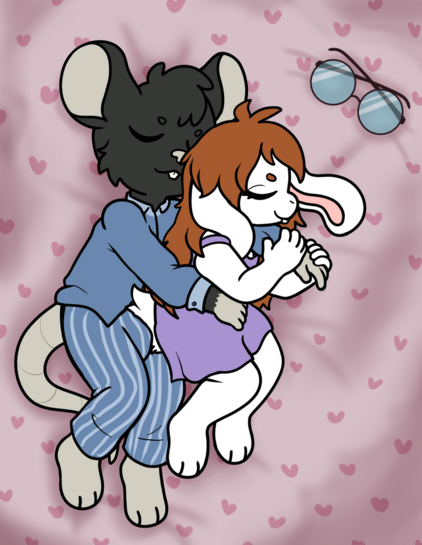
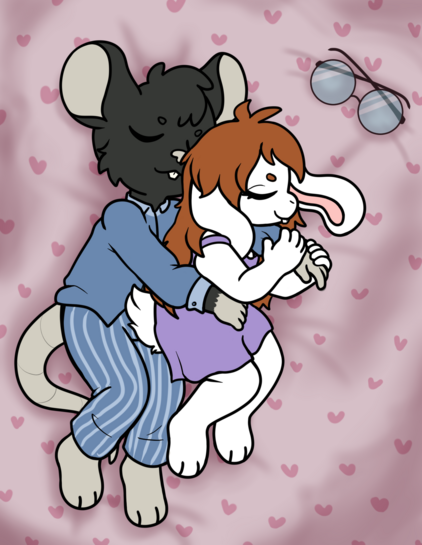
New art! It's been a bit, eh? Anyway, this one came out super cute! Big thanks to the artist, CubCore!
Rat boy: @DuckRat
Bunny girl: @Eiko
Artist: @CubCore ( https://cubcore.carrd.co/ )
(There is a NSFW version on the uncensored art site baraag: https://baraag.net/@CubCore/114385991938707908 )
Yet another mouse & rat escaped containment!
Catch them here: https://squirrelbite.com/avatars/squirrel
They are free additions if you already own the 'YA Squirrel' avatar!
sleepy... so sleepy...
#rat #rats #ratsOfMastodon #ratsOfFediverse #cute #cuteArt #OCs #OC #OCart #sona
Threat Infrastructure Uncovered Before Activation
Between November 2024 and April 2025, a set of domains and servers impersonating an Iraqi academic organization and fictitious UK tech firms were tracked. The infrastructure, while dormant, exhibited characteristics similar to APT34 (OilRig), including shared SSH keys, structured websites, and decoy HTTP behavior on M247-hosted servers. Key observations include the use of port 8080 for fake 404 responses, consistent SSH fingerprint reuse, and domains registered through P.D.R. Solutions with regway.com nameservers. The setup suggests deliberate pre-operational staging, offering defenders an early warning opportunity. Detection strategies include monitoring SSH fingerprints, HTTP response patterns, and domain registration behaviors.
Pulse ID: 68082a17ee5771aa012e93c3
Pulse Link: https://otx.alienvault.com/pulse/68082a17ee5771aa012e93c3
Pulse Author: AlienVault
Created: 2025-04-22 23:45:27
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

https://www.europesays.com/de/52215/ Nur noch mit ETA-Reisegenehmigung nach Grossbritannien: Test und Tipps #Aktualität #AktuelleNachrichten #AktuelleNews #Headlines #Konsum #Nachrichten #News #Rat #Reisen #Schlagzeilen #UK #UnitedKingdom #UnitedKingdomOfGreatBritainAndNorthernIreland #VereinigtesKönigreich #VereinigtesKönigreichGroßbritannienUndNordirland #VereinigtesKönigreichVonGrossbritannienUndNordirland
quick little reminder for me and everyone else!
#rat #rats #ratsOfMastodon #ratsOfFediverse #cute #cuteArt #OCs #OC #OCart
Chinese APT IronHusky Deploys Updated MysterySnail RAT on Russia https://hackread.com/chinese-apt-ironhusky-mysterysnail-rat-russia/ #MysterySnailRAT #Cybersecurity #CyberAttacks #CyberAttack #IronHusky #Security #Mongolia #Malware #Russia #China #RAT

Chinese APT IronHusky Deploys Updated MysterySnail RAT on Russia – Source:hackread.com https://ciso2ciso.com/chinese-apt-ironhusky-deploys-updated-mysterysnail-rat-on-russia-sourcehackread-com/ #1CyberSecurityNewsPost #CyberSecurityNews #MysterySnailRAT #cybersecurity #CyberAttacks #CyberAttack #IronHusky #Hackread #Mongolia #security #malware #Russia #China #RAT

Sticker of the Day!
This is my sticker based on my drawing of the Rat from the Chinese Zodiac!
KeyPlug-Linked Server Exposes Fortinet Exploits & Webshell Activity Targeting a Major Japanese Company
A server linked to KeyPlug malware briefly exposed tooling used in active operations. The infrastructure, live for less than a day, revealed Fortinet firewall and VPN exploit scripts, a PHP webshell, and network reconnaissance tools targeting authentication and internal portals of a major Japanese company. The exposed directory provided insight into the attacker's workflow, from infrastructure reconnaissance to post-access session management. Notable files included Fortinet reconnaissance scripts, CDN fingerprinting tools, and encrypted command execution utilities. The server's brief exposure offers a rare glimpse into the operational staging and planning of a likely advanced adversary.
Pulse ID: 6801707ed48a87a19adaf031
Pulse Link: https://otx.alienvault.com/pulse/6801707ed48a87a19adaf031
Pulse Author: AlienVault
Created: 2025-04-17 21:19:58
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

The curator's (@mathzy) angry rat.
Another member of my 'Allied Alewives' warband, she'll be in action as a 'Star Player' tomorrow in a Blood Bowl match - probably playing as Kreek Rustgouger...
Newly Registered Domains Distributing SpyNote Malware
Cybercriminals are employing deceptive websites on newly registered domains to distribute AndroidOS SpyNote malware. These sites imitate the Google Chrome install page on the Google Play Store, tricking users into downloading SpyNote, a powerful Android remote access trojan. SpyNote is used for surveillance, data exfiltration, and remote control of infected devices. The investigation uncovered multiple domains, IP addresses, and APK files associated with this campaign. The malware utilizes various C2 endpoints for communication and data exfiltration, with functions designed to retrieve and manipulate device information, contacts, SMS, and applications.
Pulse ID: 67feb504b76dd387be73309b
Pulse Link: https://otx.alienvault.com/pulse/67feb504b76dd387be73309b
Pulse Author: AlienVault
Created: 2025-04-15 19:35:32
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Forderungen und Vorschläge zur #Kommunalwahl in #Dortmund: Der DGB fordert politische Verantwortung für mehr Lebensqualität und gute Arbeit ein. #Gewerkschaft #Politik #Rat
https://www.nordstadtblogger.de/der-dgb-fordert-politische-verantwortung-fuer-mehr-lebensqualitaet-und-gute-arbeit-ein/

Malicious JScript Loader Jailbreaked to Uncover Xworm Payload Execution Flow
A new malware campaign has been identified leveraging JScript and obfuscated
PowerShell commands to deliver highly evasive malware variants XWorm and
Rhadamanthys. These threats are distributed using fileless techniques, making
them extremely difficult to detect using traditional antivirus solutions. The
campaign primarily targets Windows environments and utilizes scheduled tasks
or deceptive ClickFix CAPTCHA screens to trick users into executing malicious
payloads. Such loaders are often seen in enterprise environments, where attackers
aim to infiltrate business systems for espionage, data theft, or financial gain.
Pulse ID: 67fef516074ec94b68f3a8e7
Pulse Link: https://otx.alienvault.com/pulse/67fef516074ec94b68f3a8e7
Pulse Author: cryptocti
Created: 2025-04-16 00:08:54
Be advised, this data is unverified and should be considered preliminary. Always do further verification.