@fl : Thanks for your response!
Extremely worrysome is that Cloudflare is very USA (FISA Section 702) and MitM's all https connections: https://blog.cloudflare.com/password-reuse-rampant-half-user-logins-compromised/

@fl : Thanks for your response!
Extremely worrysome is that Cloudflare is very USA (FISA Section 702) and MitM's all https connections: https://blog.cloudflare.com/password-reuse-rampant-half-user-logins-compromised/

surely one of you #infosec peers has a guide or article on why #VPN services aren't the privacy silver bullet they often advertise themselves to be. something that mentions you're paying co-conspirators to #mitm your own traffic in addition to lowering the reputation to that of your new address space?
"Franse overheid voert phishingtest uit op 2,5 miljoen leerlingen"
https://www.security.nl/posting/881630/Franse+overheid+voert+phishingtest+uit+op+2%2C5+miljoen+leerlingen
KRANKZINNIG!
Het is meestal onmogelijk om nepberichten (e-mail, SMS, ChatApp, social media en papieren post - zie plaatje) betrouwbaar van echte te kunnen onderscheiden.
Tegen phishing en vooral nepwebsites is echter prima iets te doen, zoals ik vandaag nogmaals beschreef in https://security.nl/posting/881655.
(Big Tech en luie websitebeheerders willen dat niet, dus is en blijft het een enorm gevecht).
@mensrea : if you visit a shop (or a bank) in the center of the city, chances are near zero that it's run by impostors.
However, if you go to some vague second hand market, chances are the you will be deceived.
Possibly worse, if there's an ATM on the outside wall of a shack where Hells Angels meet, would you insert your bank card and enter your PIN?
On the web, most people do not know WHERE they are.
Big Tech is DELIBERATELY withholding essential information from people, required to determine the amount of trust that a website deserves.
DELIBERATELY, because big tech can rent much more (cheap) hosting and (meaningless) domain names to whomever if website vistors cannot distinguish between authentic and fake websites.
You are right that some people will never understand why they need to know who owns a website.
However, most people (including @troyhunt ) would enormously benefit.
Like all the other deaf and blind trolls, you trash a proposal because it may be useless for SOME, you provide zero solutions and you keep bashing me.
What part of "get lost" do you not understand?
@mensrea : it is not the UI/UX that is the problem. It is missing reliable info in the certs.
Image from https://infosec.exchange/@ErikvanStraten/114224682101772569
@aral :
I don't want to pay a cent. Neither donate, nor via taxes.
@aral : most Let's Encrypt (and other Domain Validated) certificates are issued to junk- or plain criminal websites.
They're the ultimate manifestation of evil big tech.
They were introduced to encrypt the "last mile" because Internet Service Providers were replacing ads in webpages and, in the other direction, inserting fake clicks.
DV has destroyed the internet. People loose their ebank savings and companies get ransomwared; phishing is dead simple. EDIW/EUDIW will become an identity fraud disaster (because of AitM phishing atracks).
Even the name "Let's Encrypt" is wrong for a CSP: nobody needs a certificate to encrypt a connection. The primary purpose of a certificate is AUTHENTICATION (of the owner of the private key, in this case the website).
However, for human beings, just a domain name simply does not provide reliable identification information. It renders impersonation a peace of cake.
Decent online authentication is HARD. Get used to it instead of denying it.
REASONS/EXAMPLES
Troy Hunt fell in the DV trap: https://infosec.exchange/@ErikvanStraten/114222237036021070
Google (and Troy Hunt!) killed non-DV certs (for profit) because of the stripe.com PoC. Now Chrome does not give you any more info than what Google argumented: https://infosec.exchange/@ErikvanStraten/114224682101772569
https:⧸⧸cancel-google.com/captcha was live yesterday: https://infosec.exchange/@ErikvanStraten/114224264440704546
Stop phishing proposal: https://infosec.exchange/@ErikvanStraten/113079966331873386
Lots of reasons why LE sucks:
https://infosec.exchange/@ErikvanStraten/112914047006977222 (corrected link 09:20 UTC)
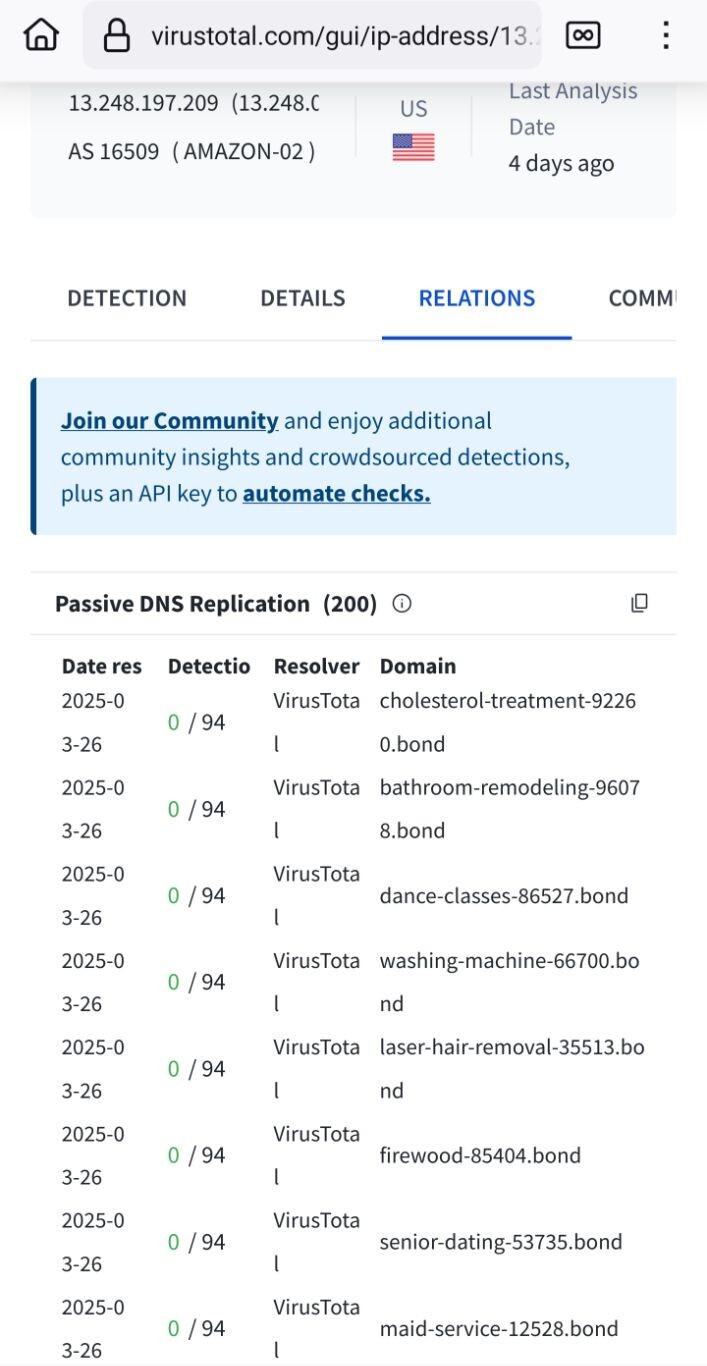
This website stopped registering junk .bond domain names, probably because there were too many every day (the last page I found): https://newly-registered-domains.abtdomain.com/2024-08-15-bond-newly-registered-domains-part-1/. However, this gang is still active, open the RELATIONS tab in https://www.virustotal.com/gui/ip-address/13.248.197.209/relations. You have to multiply the number of LE certs by approx. 5 because they also register subdomains and don't use wildcard certs. Source: https://www.bleepingcomputer.com/news/security/revolver-rabbit-gang-registers-500-000-domains-for-malware-campaigns/
@BjornW :
I've stopped doing that after a lot of people called me an idiot and a liar if I kindly notified them. I stopped, I'll get scolded anyway.
Big tech and most admins want everyone to believe that "Let's Encrypt" is the only goal. Nearly 100% of tech people believe that.
And admins WANT to believe that, because reliable authentication of website owners is a PITA. They just love ACME and tell their website visitors to GFY.
People like you tooting nonsense get a lot of boosts. It's called fake news or big tech propaganda. If you know better, why don't you WRITE BETTER?
It has ruined the internet. Not for phun but purely for profit. And it is what ruins people's lives and lets employees open the vdoor for ransomware and data-theft.
See also https://infosec.exchange/@ErikvanStraten/112914047006977222 (and, in Dutch, https://security.nl/posting/881296).
@troyhunt : if we open a website that we've never visited before, we need browsers to show us all available details about that website, and warn us if such details are not available.
We also need better (readable) certificates identifying the responsible / accountable party for a website.
We have been lied to that anonymous DV certificates are a good idea *also* for websites we need to trust. It's a hoax.
Important: certificates never directly warrant the trustworthyness of a website. They're about authenticity, which includes knowing who the owner is and in which country they are located. This helps ensuring that you can sue them (or not, if in e.g. Russia) which *indirectly* makes better identifiable websites more reliable.
More info in https://infosec.exchange/@ErikvanStraten/113079966331873386 (see also https://crt.sh/?Identity=mailchimp-sso.com).
Note: most people do not understand certificates, like @BjornW in https://mastodon.social/@BjornW/114064065891034415:
❝
@letsencrypt offers certificates to encrypt the traffic between a website & your browser.
❞
2x wrong.
A TLS v1.3 connection is encrypted before the website sends their certificate, which is used only for *authentication* of the website (using a digital signature over unguessable secret TLS connection parameters). A cert binds the domain name to a public key, and the website proves possession of the associated private key.
However, for people a domain name simply does not suffice for reliable identification. People need more info in the certificate and it should be shown to them when it changes.
Will you please help me get this topic seriously on the public agenda?
Edited 09:15 UTC to add: tap "Alt" in the images for details.
@Linux : you're definitely not fearmongering.
Eugene Kaspersky warned many times for fragmentation of the internet, like in https://www.smh.com.au/technology/cyber-spying-risks-the-future-of-the-internet-eugene-kaspersky-20131107-hv2g1.html more than 11 years ago:
❝
Mr Kaspersky said he feared governments would withdraw to their own parallel networks away from the prying eyes of others, and would cease investing in the development of the public internet, products and services.
❞
(An IMO nice read on internet history: https://eugene.kaspersky.com/2017/02/07/internet-archaeology/).
Personally I predicted many years ago that online identity fraud would cause too much damage soon.
Fortunately both predictions have not fully materialized, but we're definitely heading in the wrong direction.
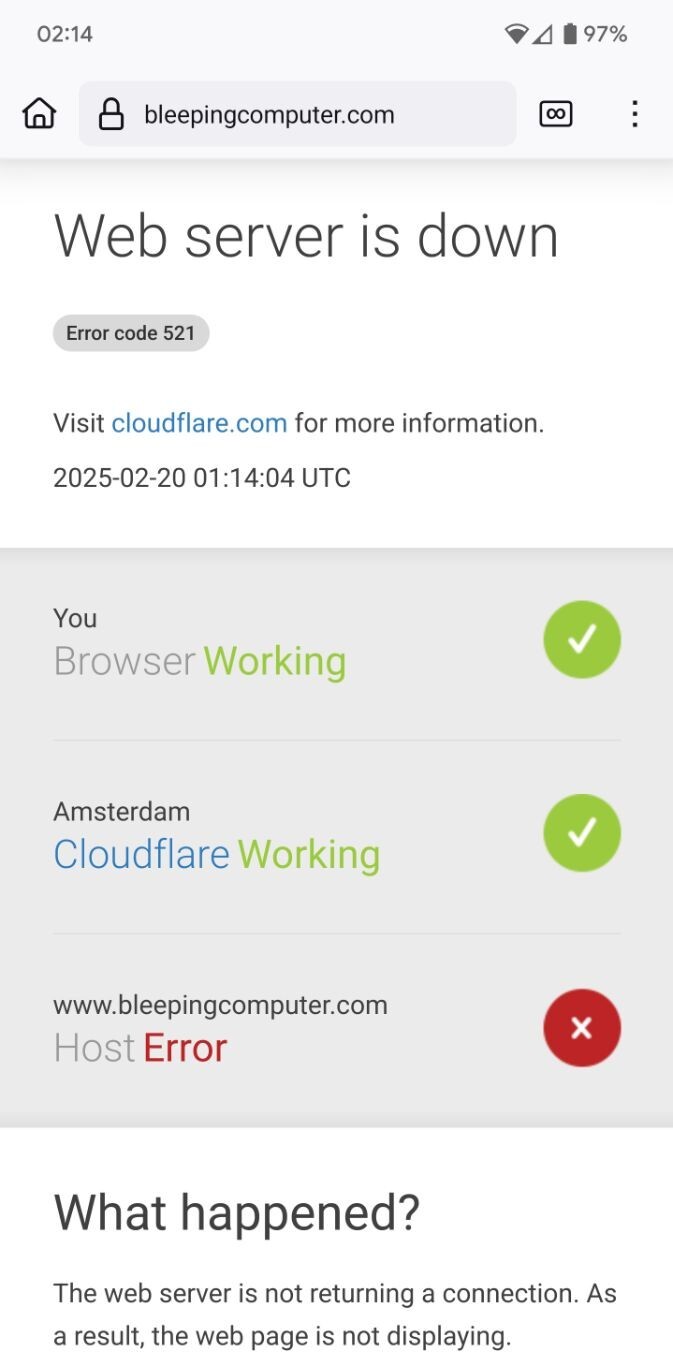
Here's one example from many, severly undermining trust in the internet: https://www.bleepingcomputer.com/news/security/microsoft-trust-signing-service-abused-to-code-sign-malware/.
It's not just TLD's: by far most digital certificates are issued by Big Tech with pompous names like "Google Trust Services" - most of them to criminal websites.
See also https://gist.githubusercontent.com/qbourgue/071c333ff5182f031da3ba55cc7da1ec/raw/ec4ba396c0d1052cc8b0a69c1bad1e0e5aef2ab6/malicious_domains_impersonating_reddit_wetransfer_selfau3_dropper_lumma_stealer_20012025.txt (src: @_r_netsec in https://infosec.exchange/@_r_netsec/114211978370291738).

Dankjewel voor deze verhelderende uitleg. Ik heb er niet bij stilgestaan dat door Cloudflare grote blokken van het internet letterlijk kunnen worden uitgeschakeld, door simpelweg een script te draaien
@cR0w @troyhunt @dangoodin @benjojo @Viss @matthew_d_green
Seriously, #ClownFlare are at best a #ValueRemoving #MITM and more often than not a #RogueISP who's business model is a #RacketeeringScheme that should not exist to begin with.
@0xF21D #ClownFlare is a #RogueISP and their #MITM-based approach eould've always allowed that.
@0xF21D : Cloudflare is evil anyway.
Cloudflare reverse-proxies (or -proxied):
-
cloudflare.com.save-israel·org
-
ns.cloudflare.com.save-israel·org
-
albert.ns.cloudflare.com.save-israel·org
-
sydney.ns.cloudflare.com.save-israel·org
-
I don't know whether any of these domains were or are malicious, but such domain names are insane; expect evilness.
See also:
https://crt.sh/?Identity=save-israel.org
Tap "Alt" in the images for more info.
@0xF21D wrote: "[...] something we technically knew was going on before but didn't consciously consider a threat, until now."
I've been warning for CDN's like Cloudflare and Fastly (and cloud providers in general) for a long time.
Here's a recent toot (in Dutch, the "translate" button should do the job): https://infosec.exchange/@ErikvanStraten/114042082778156313.
If you trust Google to translate it (guaranteed NOT error-free, it *may* work in other browsers than Chrome): https://infosec-exchange.translate.goog/@ErikvanStraten/114042082778156313?_x_tr_sl=nl&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=wapp
P.S. Fastly knows your https://infosec.exchange login credentials.
https://arcanechat.me server reached 1500 users!!!
the server is using around 1GB of RAM, CPU is almost unused, and only 1.4GB of storage used for encrypted user volatile data, that is around 1MB per user on average!
the cost of self-hosting a #chatmail server for #ArcaneChat / #DeltaChat is really low! and you don't even need to trust the server operator or even the VPS provider if you are selfhosting since all is #e2ee and safe against #mitm thanks to the green checkmark in chats

Uh, if that's Schrodinger's mouse, then clearly it's a Quantum MITM attack!!!
You need PQCs now!!! (Pest Quelling Cryptography)
@torproject same with #obfs4 bridges: there is no option to say like ports=80,443 or similar, which makes it cumbersome to get said bridges.
And trying to get places to #DontBlockTor that criminalize the use of #Tor is foolish at best.
@SandraDeHaan schreef: "Ook NL heeft zich afhankelijk gemaakt van Amerikaanse digitale infrastructuur (o.a. cloud-diensten)."
Daar waarschuw ik al langer voor (zie https://security.nl/posting/684958 van 6-1-2021 toen ik de bestorming van het Capitool zag, en zie bovenaan die pagina).
En gisteren nog: https://infosec.exchange/@ErikvanStraten/114042082778156313
En de NL overheid gaat daar, op advies van "experts" (anoniem natuurlijk) gewoon in mee: https://security.nl/posting/876914.
Hoe NAÏEF kunnen we zijn?!
En waarom een EV-certificaat, bijv. van de Rabobank, 1FA (en DV nauwelijks veiliger dan DNS is - een notoir onveilig protocol): https://security.nl/posting/877247.
P.S. Helaas heb ik Bert Hubert moeten bliokken nadat hij IDF-propagandaspam uit Auschwitz had geboost.
#Availability #Beschikbaarheid #Cinfidentiality #Vertrouwelijkheid #Integrity #Integriteit #Authenticity #Authenticiteit #Risico #Economie #Cloudflare #Fastly #CDN #AitM #MitM.#FISASection702 #FISA #ThreeLetterAgencies#Trump #Sbowden #E2EE #InfoSec #VVD #PVV #CIDI #VT #VirusTotal #DVCerts #DV #OV #EV #QWAC #CyberCrime #NepWebsites #FakeWebsites