#EncryptHub's dual life: Cybercriminal vs #Windows bug-bounty researcher
Frühere Suchanfragen
Suchoptionen
#encrypthub
Imagine a hacker who not only exploited zero-days to breach over 600 organizations but also played the hero by patching vulnerabilities for Microsoft. How does one person walk the line between cybercrime and cybersecurity?
https://thedefendopsdiaries.com/decrypting-encrypthub-a-cybersecurity-enigma/
#cybersecurity
#encrypthub
#bugbounty
#ethicalhacking
#cybercrime

The controversial case of the threat actor EncryptHub – Source: securityaffairs.com https://ciso2ciso.com/the-controversial-case-of-the-threat-actor-encrypthub-source-securityaffairs-com/ #rssfeedpostgeneratorecho #informationsecuritynews #ITInformationSecurity #SecurityAffairscom #CyberSecurityNews #PierluigiPaganini #SecurityAffairs #SecurityAffairs #BreakingNews #SecurityNews #hackingnews #CyberCrime #Cybercrime #EncryptHub #hacking #Malware

The controversial case of the threat actor #EncryptHub
https://securityaffairs.com/176251/cyber-crime/the-controversial-case-of-the-threat-actor-encrypthub.html
#securityaffairs #hacking
(trendmicro.com) A Deep Dive into Water Gamayun's Arsenal and Infrastructure https://www.trendmicro.com/en_us/research/25/c/deep-dive-into-water-gamayun.html
Executive Summary:
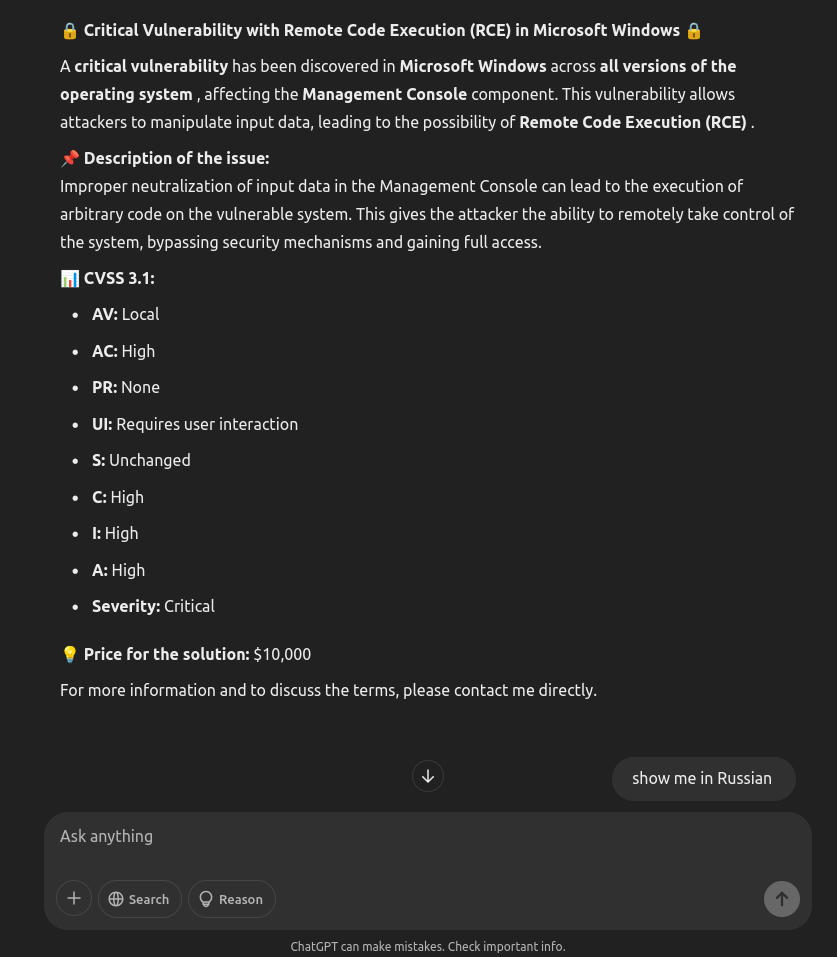
This research provides a comprehensive analysis of Water Gamayun (also known as EncryptHub and Larva-208), a suspected Russian threat actor exploiting the MSC EvilTwin zero-day vulnerability (CVE-2025-26633) in Microsoft Management Console. The threat actor employs sophisticated delivery methods including malicious provisioning packages, signed MSI files, and Windows MSC files to deploy multiple custom payloads. Their arsenal includes custom backdoors (SilentPrism and DarkWisp), multiple variants of the EncryptHub Stealer, and known malware like Stealc and Rhadamanthys. The research details the C&C infrastructure, data exfiltration techniques, and persistence mechanisms used by the group. Trend Micro researchers gained access to the C&C server components, enabling them to analyze the architecture, functionality, and evasion techniques employed by the threat actor.

Russian Ransomware Gang Exploited Windows Zero-Day Before Patch – Source: www.securityweek.com https://ciso2ciso.com/russian-ransomware-gang-exploited-windows-zero-day-before-patch-source-www-securityweek-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #Malware&Threats #vulnerabilities #securityweekcom #CVE-2025-26633 #securityweek #EncryptHub #ransomware #TrendMicro #Microsoft #MMC

EncryptHub Exploits Windows Zero-Day to Deploy Rhadamanthys and StealC Malware – Source:thehackernews.com https://ciso2ciso.com/encrypthub-exploits-windows-zero-day-to-deploy-rhadamanthys-and-stealc-malware-sourcethehackernews-com/ #rssfeedpostgeneratorecho #CyberSecurityNews #TheHackerNews #EncryptHub

Russian Ransomware Gang Exploited Windows Zero-Day Before Patch https://www.securityweek.com/russian-ransomware-gang-exploited-windows-zero-day-before-patch/ #Malware&Threats #Vulnerabilities #CVE202526633 #Ransomware #EncryptHub #ransomware #TrendMicro #Microsoft #MMC
Russian Ransomware Gang Exploited Windows Zero-Day Before Patch https://www.securityweek.com/russian-ransomware-gang-exploited-windows-zero-day-before-patch/ #Malware&Threats #Vulnerabilities #CVE202526633 #Ransomware #EncryptHub #ransomware #TrendMicro #Microsoft #MMC
EncryptHub’s OPSEC Failures Expose Its Malware Operation https://hackread.com/encrypthub-opsec-failures-expose-malware-operation/ #Cybersecurity #CyberCrime #EncryptHub #Security #security #Malware #XSSIS

Researchers have uncovered #EncryptHub cybercrime gang's multi-stage malware campaign, exposing its infrastructure and tactics due to critical OPSEC failures.
Read: https://hackread.com/encrypthub-opsec-failures-expose-malware-operation/

#EncryptHub breaches 618 orgs to deploy infostealers, #ransomware



